Cloud
Secure Connectivity in Azure
14 March 2023 • 4 min read

Cloud computing has greatly expanded the options available to organisations for running web applications, file storage, database hosting and many other areas. It has brought new types of resources as well as new ways of provisioning those that are more familiar. For Azure-based SQL services there are the options to run on a Virtual Machine or ‘platform as a service’ (PaaS) options–including Azure SQL Server.
Organisations also need to balance these new possibilities with their information security posture, especially those in regulated industries such as government, utilities, and financial services. The requirements might include that data is encrypted in transit or is not accessed over the internet. With Azure, options are available to satisfy such requirements.
We will explore the options available to connect more securely, both in general to Azure as a whole and then - through the lens of SQL Server - the options available for specific types of resource.
Options Connecting to the Azure Boundary
As well as the default method to connect over the internet, the following options exist:
|
Option |
Suitability |
Security Details |
|
Point to Site (P2S) VPN |
Small number of people working on a proof of concept |
Encrypted connection over internet from individual laptops terminating directly within an organisation’s private IP space in Azure. |
|
Site to Site (S2S) VPN |
SMEs and specific use cases |
Encrypted connection between the organisation’s network and their private IP space in Azure. Facilitates integration of on-premises private IP space and systems such as DNS and Active Directory. |
|
ExpressRoute |
Large scale production workloads with high-speed connectivity (up to 100 Gbps) |
The enhanced functionality of S2S VPN but on a stable, low latency and secure private connection. Allows use of Azure as an extension of the organisation’s data centre. |
The above options can be combined, for example a S2S VPN and an ExpressRoute connection can coexist. ExpressRoute is a private connection but is not encrypted. If–for compliance reasons–an encrypted connection must be used, then a second connection using a S2S VPN is an option.
Using any of the above options gives us the ability to reach out privately, however, how do we make resources designed to be accessed over the internet reachable in this way? How can we restrict access to these resources just to be reachable privately?
Private Connectivity to Azure SQL
SQL Server on VM
An Azure VM, running SQL Server will have a private IP address in a virtual network. An ExpressRoute or VPN connection into the same or a peered virtual network makes direct private IP connectivity possible. An application running on-premises could connect to the database without needing to use a public IP address, even indirectly via NAT. This means the VM need not be assigned a public IP address and the database can be inaccessible from the internet.
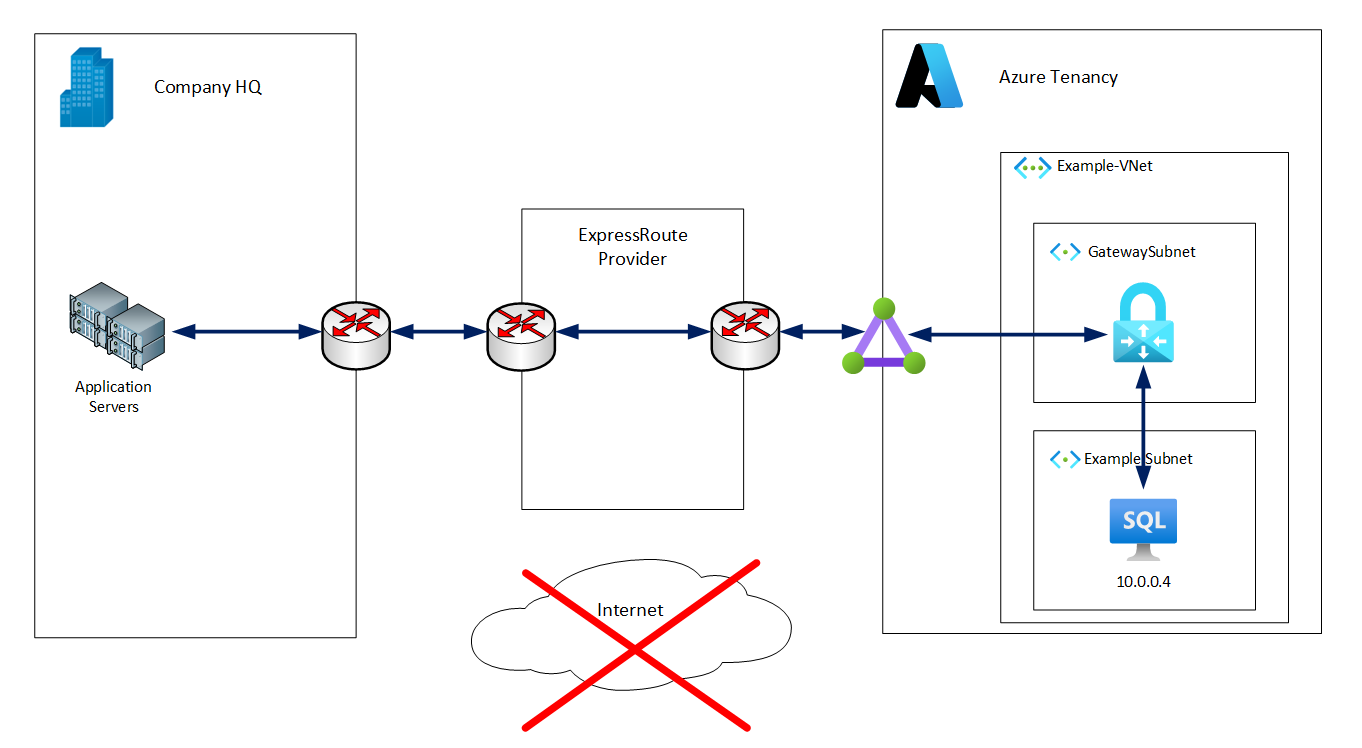
SQL Server PaaS Options
Private Endpoints
A Private Endpoint can be thought of as connecting a network interface to an Azure PaaS service instance and attaching it to a virtual network. The result is that the specific instance of the PaaS service can now be accessed via a private IP address. A configured private endpoint can be seen with a corresponding IP Address and in further detail below.
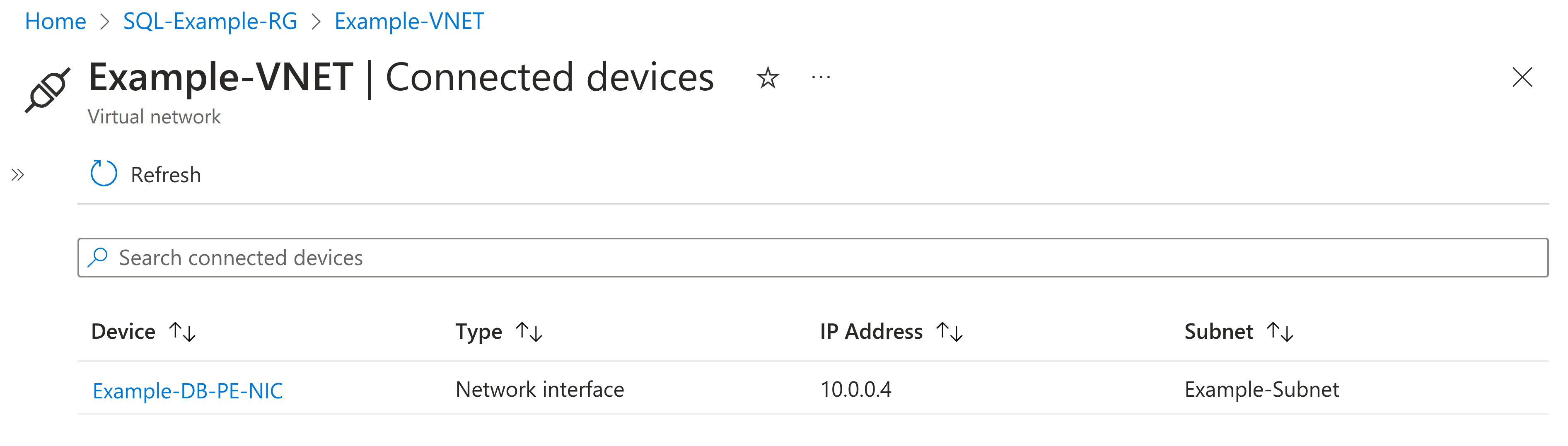
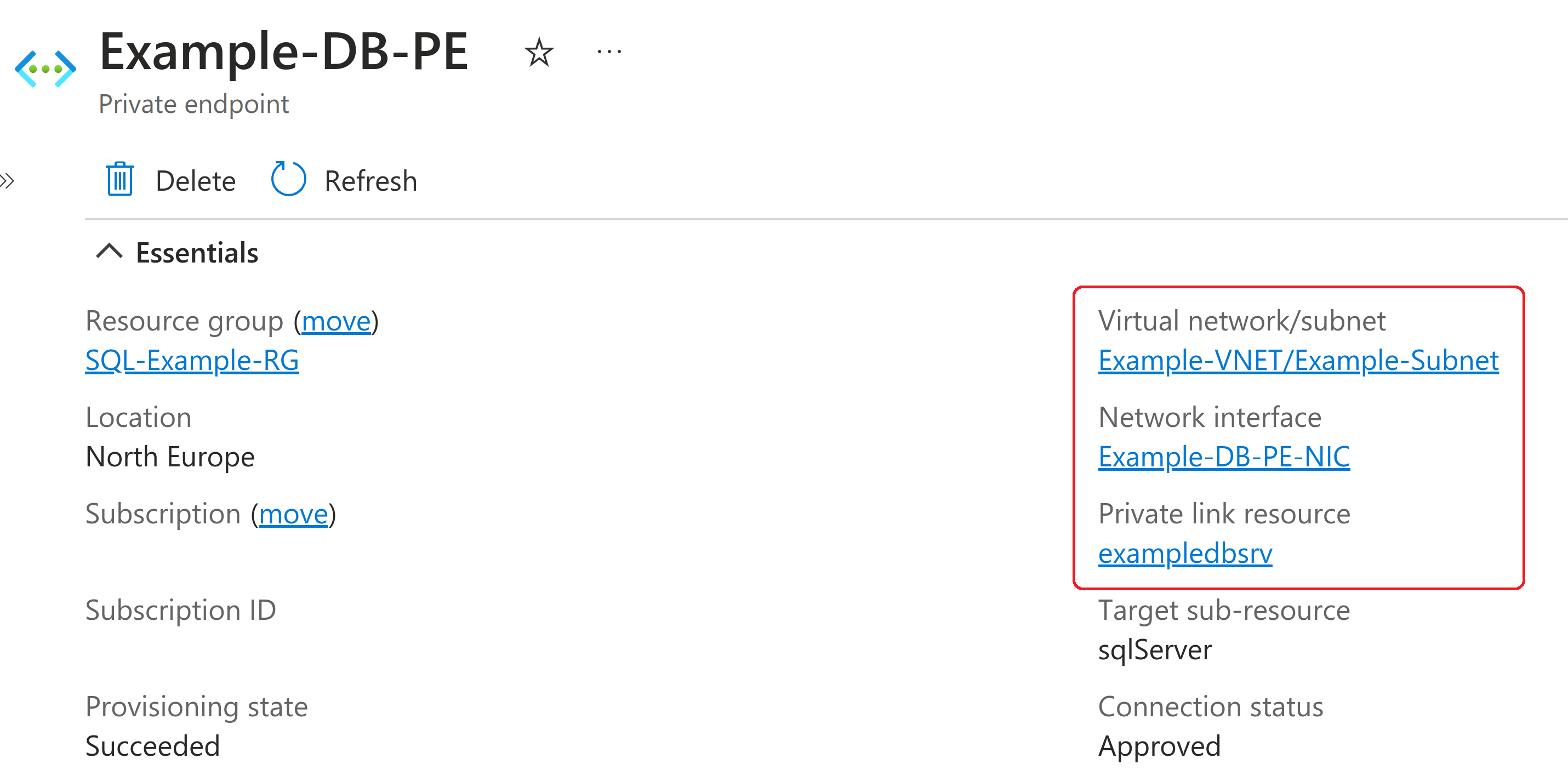
Although PaaS services are natively accessible via the internet, they can be locked down partially or completely, e.g.:
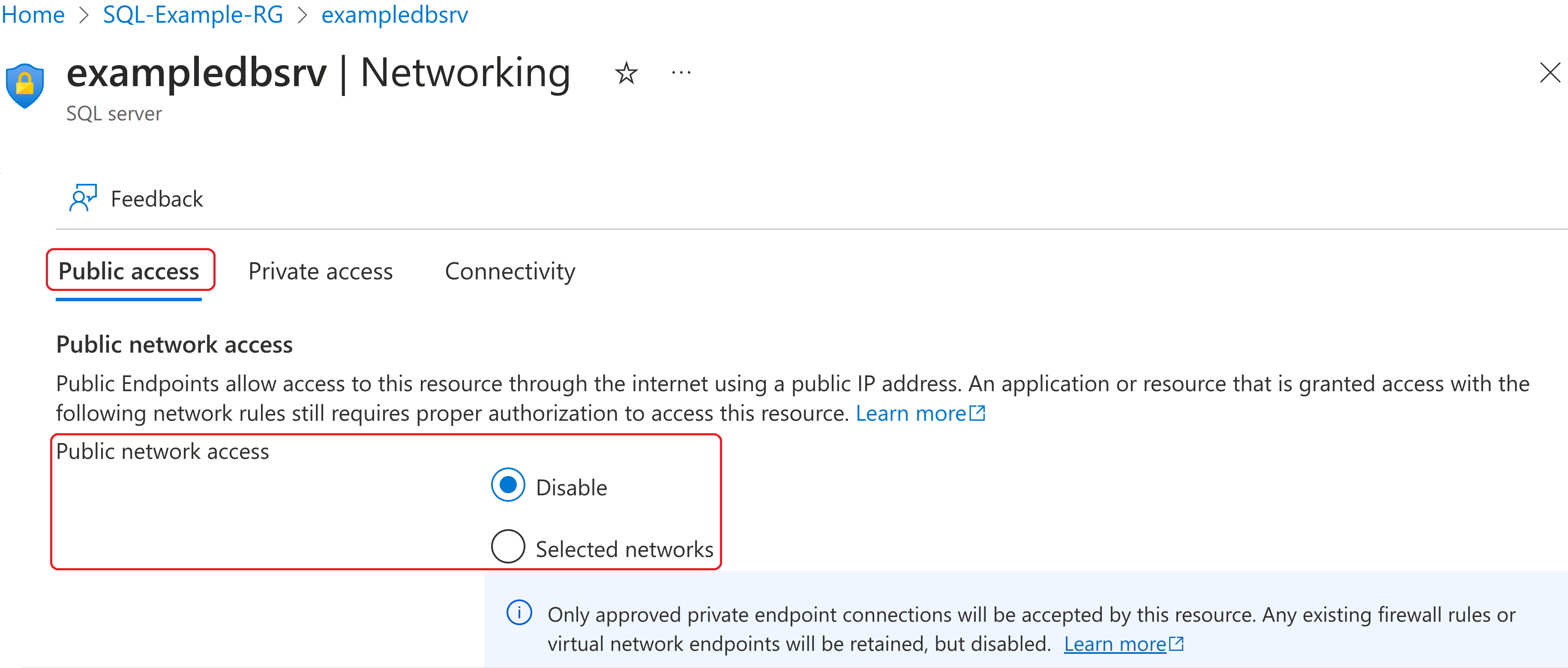
Private Endpoints enable direct private IP connectivity from on-premises to an Azure PaaS database in the same way as to a VM.
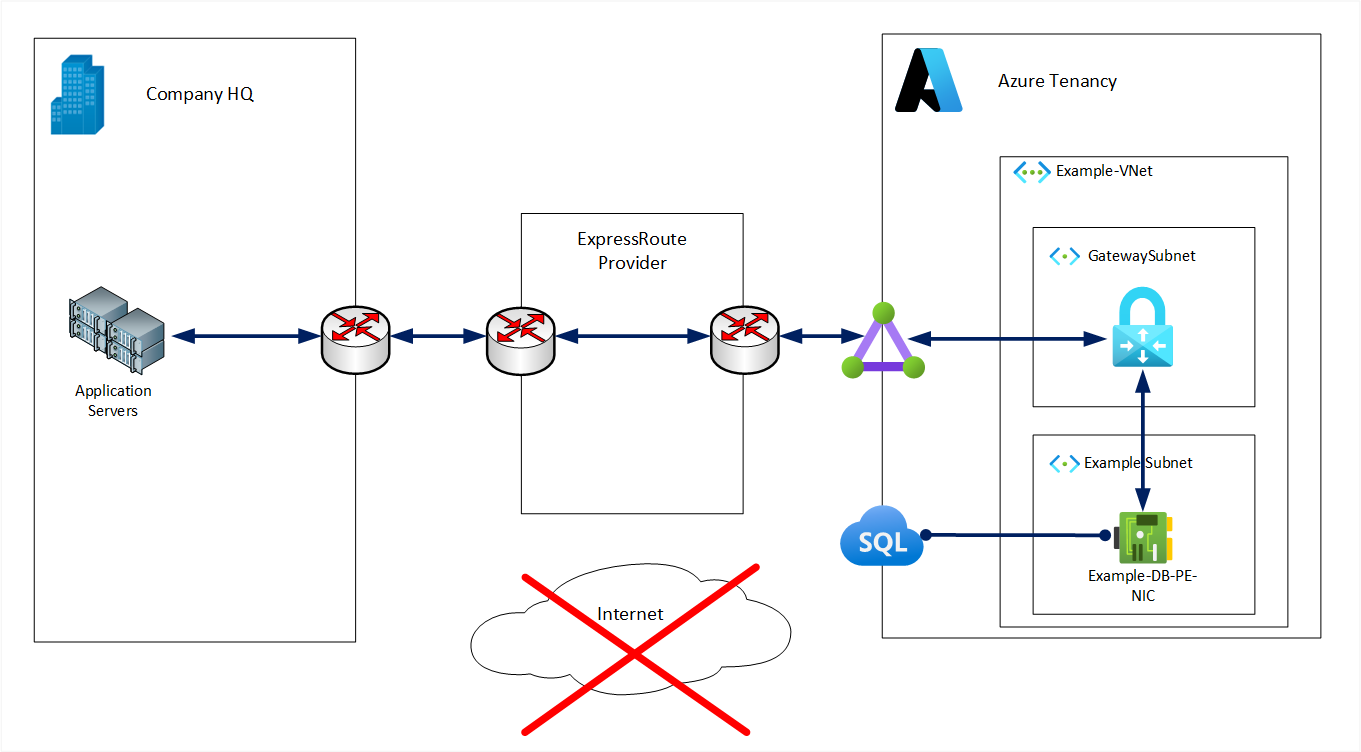
In both examples, the same outbound private connectivity can also be initiated from applications running in Azure.
Service Endpoints
Service Endpoints are an additional option for Azure to Azure connections and are created at the subnet level on an entire PaaS service basis, e.g.:
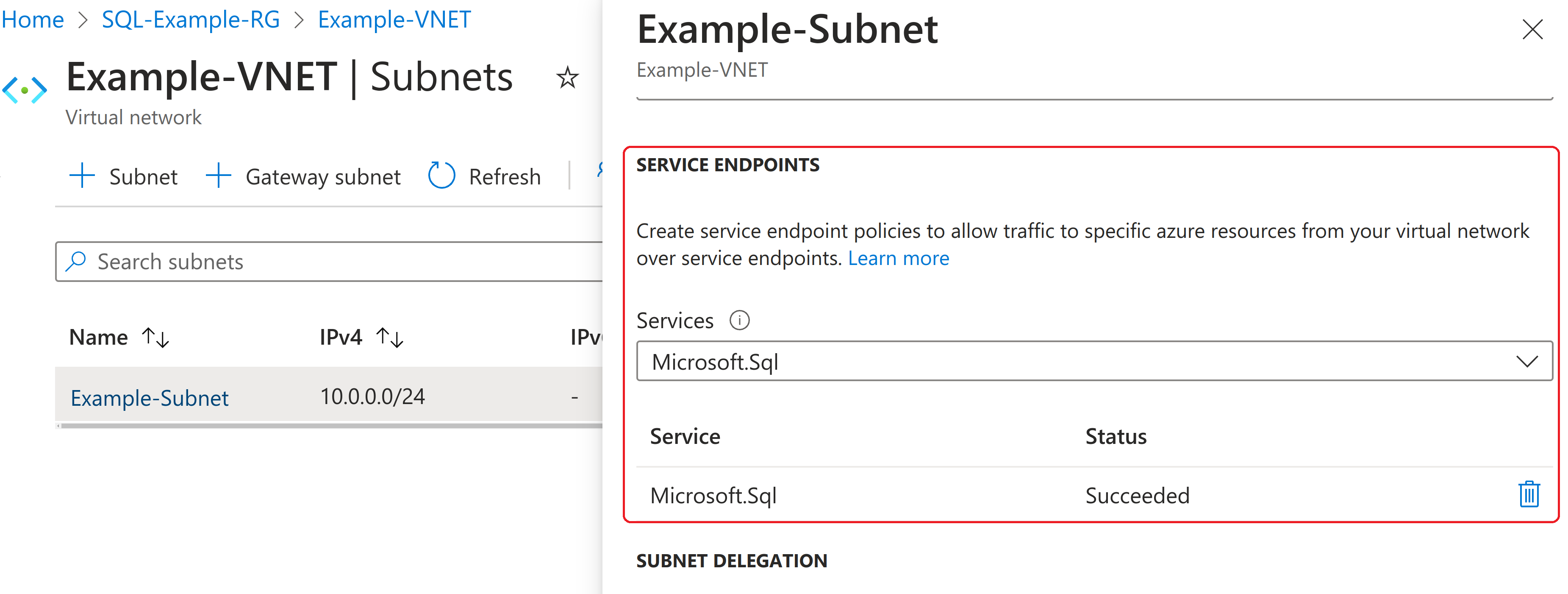
Service Endpoints don’t provide private IP addresses, instead directing traffic from the subnets enabled for that service via a secure optimised route over the Azure backbone ending at a public IP address.
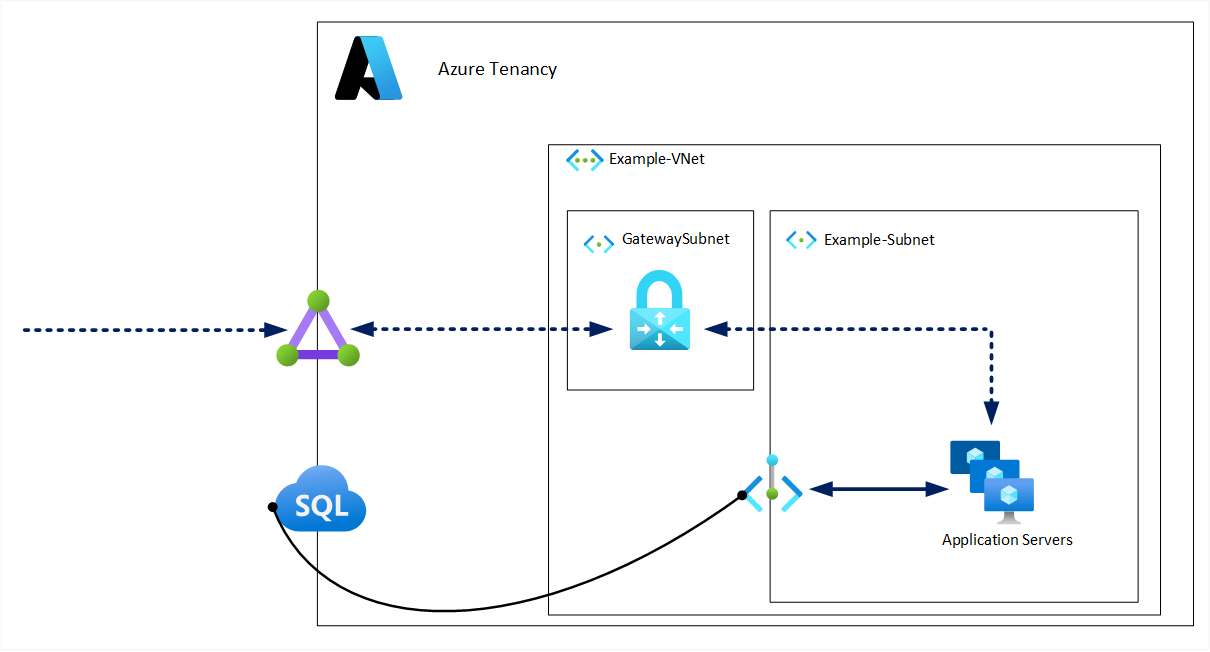
Although public IP addresses are still used, it’s possible to restrict access only to the virtual networks you specify as shown below:
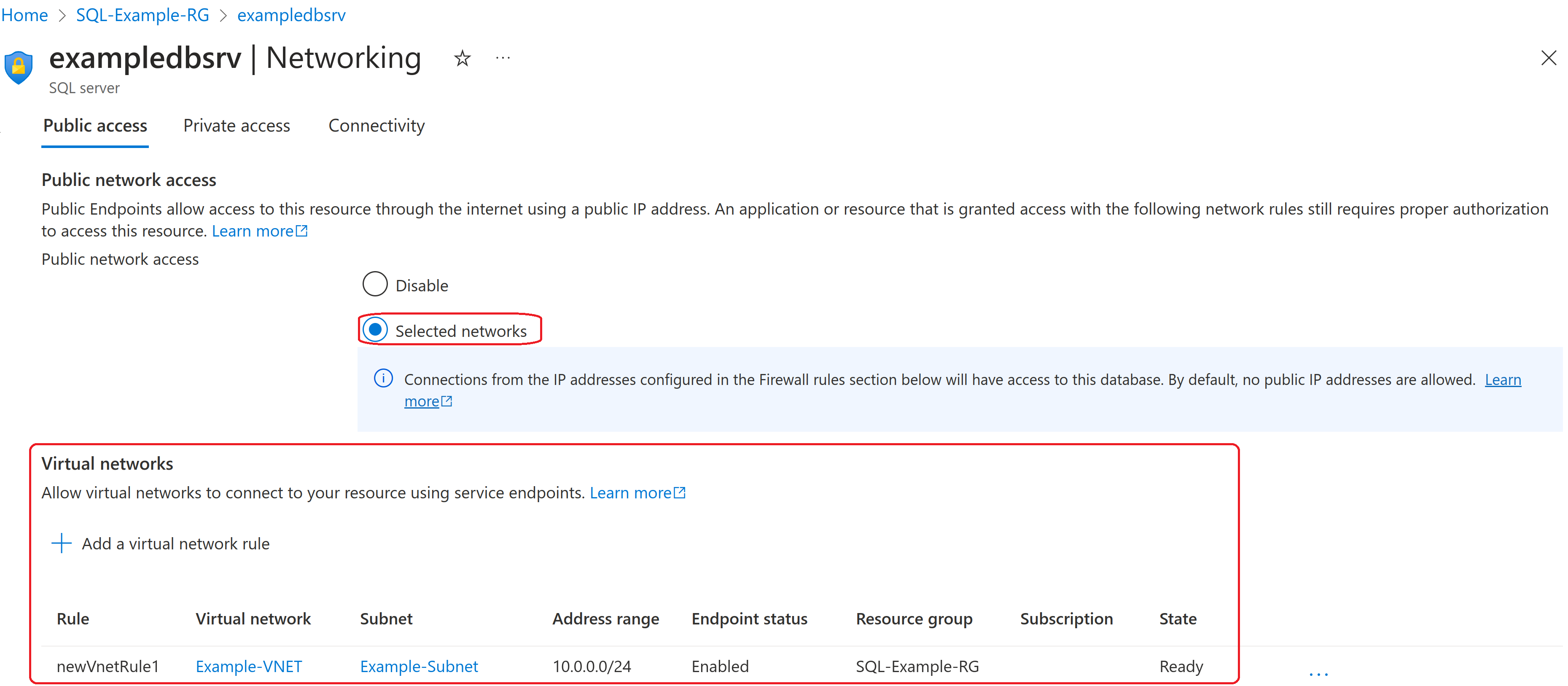
Service Endpoints come at no extra cost (unlike Private Endpoints) but don’t support access from on-premises. If the requirement is to reduce or remove public exposure of the SQL PaaS instance but connectivity is only needed from within Azure then Service Endpoints can be the most cost-effective option.
Conclusion
Service Endpoints and Private Endpoints are also applicable for a range of storage, application, big data and AI services in Azure. We have seen above how these provide a more secure way to connect to Azure PaaS resources. Furthermore - when coupled with either a VPN or an ExpressRoute connection - this secure connectivity can extend from on-premises as well as from within Azure.
There are also many other solutions including those to privately connect one Azure PaaS service to another, within and between tenancies. To supplement these private connectivity methods Azure also provides a range of Firewall options to further secure your resources. Taking advantage of the possibilities of cloud computing and maintaining your information security posture can be done.



